Connection Setup
Follow this guide to setting up SSH on your computer
Background Information
To establish a secure connection through which we can access MOGON on our local computer, the Secure Shell (SSH) protocol comes into play. The central aspect of SSH is a pair of cryptographically generated keys—a public and a private key.
As the name suggests, you can share your public key without concern—feel free to tell it to your neighbor. On the other hand, you should always keep your private key secret! While the public key can be transferred to MOGON through a potentially unsafe network, the private key will never leave its place. Even during authentication it stays on your local machine.
How do these keys help with authentication? Well, the public key can encrypt a message that only your matching private key can decrypt. So, imagine MOGON sends you a message that has been encrypted using your own public key. You can now prove your identity just by decrypting it! After all, you are the only person in the world that has the matching private key.
You can connect to MOGON without studying cryptography, though. Just follow the steps described below.
- Ask your PI to add your JGU account to an HPC project.
- Generate your SSH keys using Windows or Linux/macOS.
- Add your public SSH key to your JGU account as demonstrated here.
Generating SSH Keys on Windows
Here we provide information on how to create SSH keys on Windows with different tools.
Open Windows PowerShell. Press the key, type
PowerShelland hit enter.Check if
OpenSSHis installed on your system:ssh -VYou should get an output similar to that shown below
OpenSSH_for_Windows_7.7p1, LibreSSL 2.6.5This tutorial was created with the
OpenSSH versionshown above andPowerShell 7.0.2.Start the
ssh-agentif it is not running already:Start-Service ssh-agentGo to the
.sshdirectory of your user home:cd ~\.ssh\Generate a new SSH key pair with the
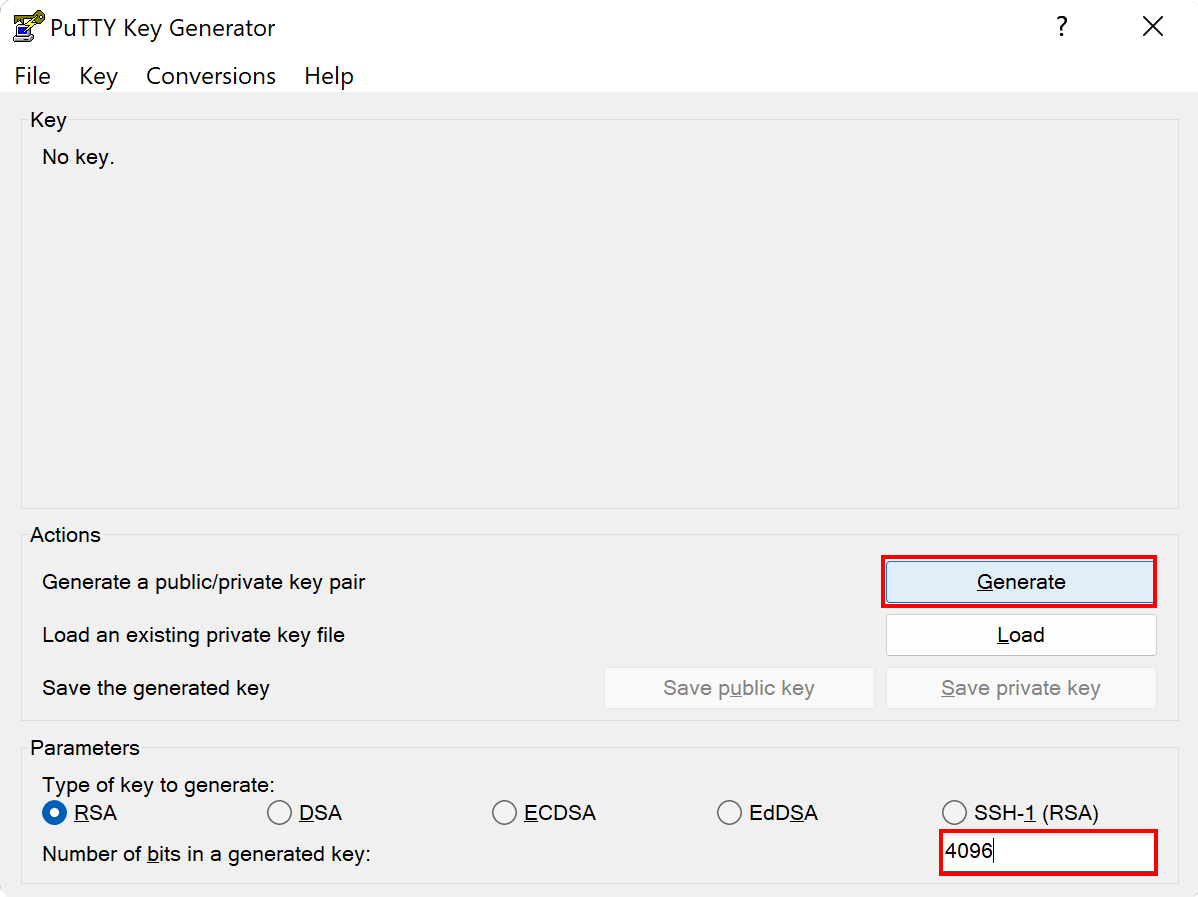
ECDSAalgorithm:ssh-keygen -t ecdsa -b 521 -C "HPCGATE,HPCLOGIN"For compatibility reasons make sure to use the ECDSA algorithm. The RSA algorithm used by Windows is old compared to the RSA algorithm used on MOGON. This causes conflicts and prevents a connection from being established.
Then
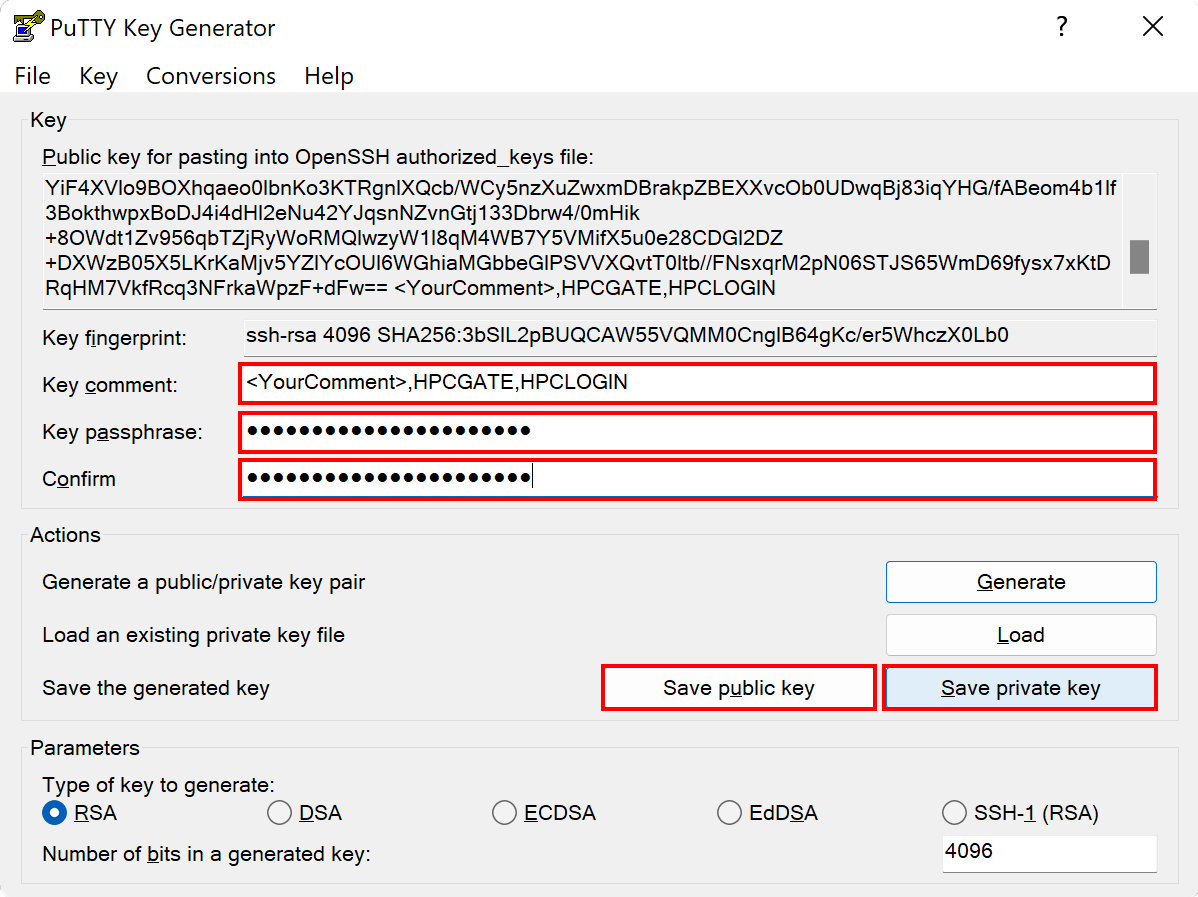
ssh-keygenasks for a name for the key.Enter a file in which to save the key (/home/you/.ssh/id_ecdsa): [Press enter]After that you have to specify a passphrase. Do not use an empty passphrase!
Enter passphrase (empty for no passphrase): [Type a passphrase] Enter same passphrase again: [Type passphrase again]Done. You have created an SSH key that will allow you to access MOGON using PowerShell. Upload you public SSH key to your JGU account
Generating SSH Keys on Linux/macOS
Generating an SSH key pair can be as easy as executing the following command in your terminal:
ssh-keygen -t ed25519 -C "HPCGATE,HPCLOGIN"This generates a new key pair of type ed25519. The comment "HPCGATE,HPCLOGIN" is mandatory and lets our webtool in a later step know where to put your public key.
Next, ssh-keygen prompts you to enter a name for the key files.
Enter a file in which to save the key (/home/you/.ssh/id_ed25519): [Press enter]You can press enter to confirm the default or provide an alternative. A meaningful name might be /home/<user>/.ssh/id_ed25519_mogon_laptop.
After that you have to specify a passphrase—use a passphrase! An empty passphrase is a serious security concern.
Enter passphrase (empty for no passphrase): [Type a passphrase]
Enter same passphrase again: [Type passphrase again]In case you deviate from the default name, you need to make your ssh-agent aware of it by executing:
ssh-add ~/Path/To/Your/PrivateKeyModifying existing SSH Keys
If you already have an SSH key pair, you can change the comment as follows, for example, to add the HPCGATE,HPCLOGIN string if you have forgotten to append it:
ssh-keygen -c -C "HPCGATE,HPCLOGIN" -f ~/Path/To/Your/PrivateKeyCreating an SSH Configuration File
If you need to login from the outside more often, you can configure your SSH client to perform these steps automagically.
For this purpose, edit your local SSH config (~/.ssh/config) to include the following lines, where the setting ForwardX11 yes is optional:
# MOGON jump host
Host hpcgate
HostName hpcgate.zdv.uni-mainz.de
User <username>
ForwardX11 yes
IdentityFile ~/Path/To/Private/Key
# for access to MOGON II:
Host mogon
HostName mogon
User <username>
ProxyJump hpcgate
ForwardX11 yes
IdentityFile ~/Path/To/Private/Key
# for access to MOGON NHR:
Host mogon-nhr
HostName mogon-nhr-01
User <username>
ProxyJump hpcgate
ForwardX11 yes
IdentityFile ~/Path/To/Private/KeyUser and IdentityFile options!ssh mogonfor access to a service node on MOGON II, or:
ssh mogon-nhrto connect with MOGON NHR.
(More information on the jumphost technique with ProxyCommand here )
Config for OpenSSH below version 7.3
# MOGON jump host
Host hpcgate
HostName hpcgate.zdv.uni-mainz.de
User <username>
IdentityFile ~/Path/To/Private/Key
# for access to MOGON:
Host mogon
HostName mogon
User <username>
IdentityFile ~/Path/To/Private/Key
ProxyCommand ssh -W %h:%p hpcgateUsing X11-forwarding on MacOS
In order to use the X11-forwarding, an X11-server should be installed on your system. X11 is no longer included with Mac, but X11 server and client libraries are available from the XQuartz project .
Uploading the Public Key
- Ask your PI to add your JGU account to an HPC project.
- Generate your SSH keys using Windows or Linux/macOS.
- Add your public SSH key to your JGU account as demonstrated here.
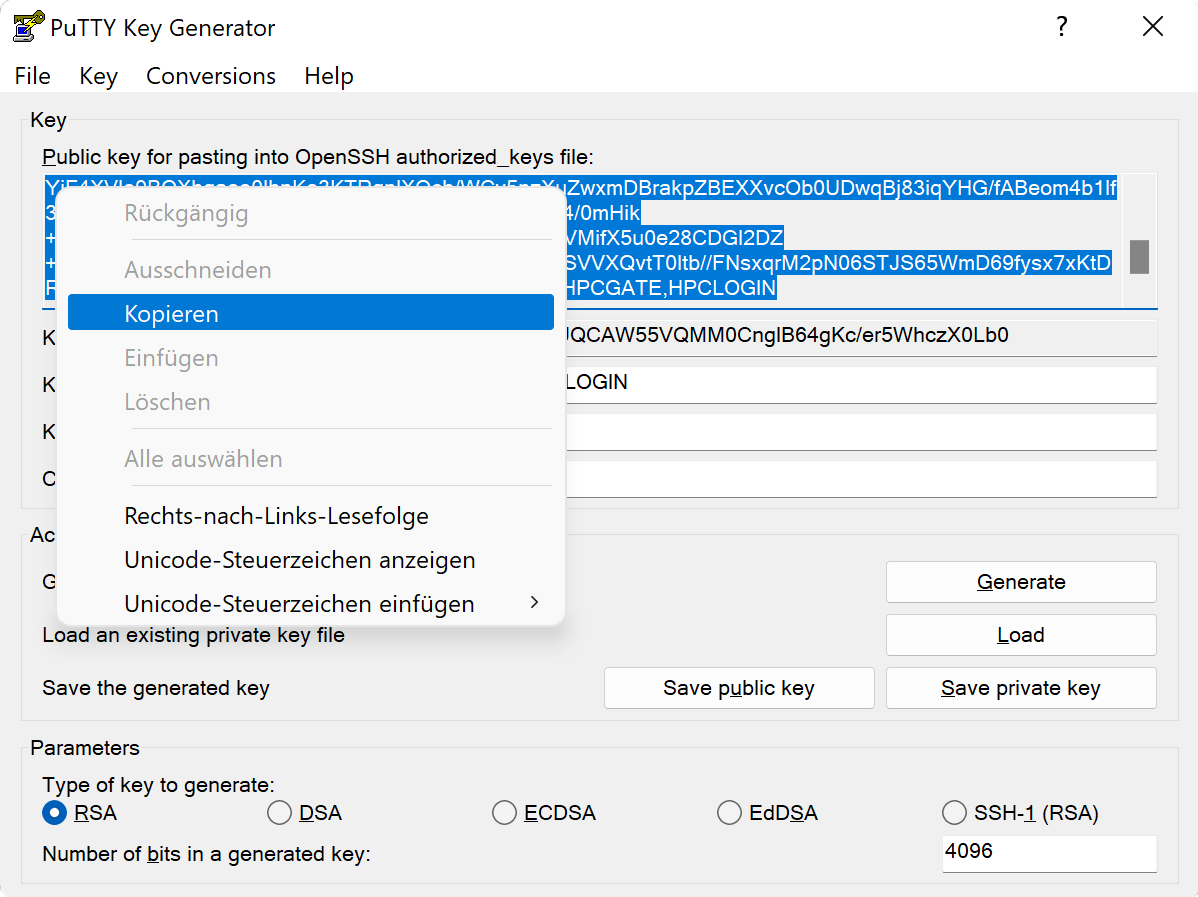
To make MOGON aware of your new SSH key, we use a web-tool to transfer the public key to the server. Please note that it takes some time for these changes to propagate through our systems. During working hours it should take no more than 20 minutes.
- Browse to
account.uni-mainz.de
and use your
JGU credentialsfor login. - Paste the contents of your public SSH key into the
SSH public keyfield. - You can add further comments in the
Comment or key namefield to help you identify this key again at a later point in time. - Please select
HPCLOGINas thekey usage. - Feel free to leave the duplicate
HPCLOGINas is, or delete it from the public key field. - At last, please click on
Save. - The newly added SSH key should be displayed in the SSH key overview.